The English version of Wikipedia is the website that tops the search results for a large majority of popular search terms. How do you keep 140,000+ active editors happily producing good content in a neutral way when they all have opposing viewpoints on content and procedure?
“Wikipedia is like a sausage: you might like the taste of it, but you don’t necessarily want to see how it’s made.”—Jimmy Wales
The Arbitration Committee
B asically the Supreme Court of Wikipedia, the Arbitrators that make up the committee make decisions on Wikipedia disputes that haven’t been able to be resolved through other means or on issues where privacy needs to be protected. Jimmy Wales and The Wikimedia Foundation are essentially the only people above them. They largely conduct business over a private mailing list, potentially to appear in agreement in public. Abd says:
asically the Supreme Court of Wikipedia, the Arbitrators that make up the committee make decisions on Wikipedia disputes that haven’t been able to be resolved through other means or on issues where privacy needs to be protected. Jimmy Wales and The Wikimedia Foundation are essentially the only people above them. They largely conduct business over a private mailing list, potentially to appear in agreement in public. Abd says:
“[the] appearance [of solidarity] was more important than making the whole process transparent, so that the community could understand the logic or reasons behind decisions — for better or worse.”
Arbitrators receive access to the CheckUser and Oversight tools, which gives them access to IP and user agent records and the ability to expunge content from an article’s history, respectively.
List structure and security
The mailing list software emailed each list member their password in plain text every month. Someone gaining access to one of their email accounts, say by using Firesheep over an unsecured WiFi connection, would’ve easily gained access to the private archives. No selective archiving was available in the software, so everything was logged. It doesn’t seem like it would have been difficult for a list member to intentionally leak the contents of the archive (although it appears to be easier for unauthorized users to access the archive than the authorized: “I will take care of that if I can get into the archives, it often doesn’t work for me”). Because of the nature of email it is easy to accidentally send something to the wrong person, illustrated in one of the emails leaked where someone was accidentally carbon copied in on an email about them. Retired arbitrators continued to have access to the list until sometime around 2009. Jimmy Wales continues to have access to the list.
Wikipedia editors generally expect their IP addresses to be protected when they’re logged in and policy supports this assumption (although in reality I’m unsure why IPs are considered such private information). CheckUser records only go back so far so it would be interesting to see what privacy concerns were considered by individuals keeping their own records. It also appears that centralized information on troublesome users is kept on a private wiki.
“Unitanode is formerly known as SDJ (S. Dean Jameson), and has had prior accounts as well. See the WPuser page on the arbwiki.”
“The earlier draft would, incidentally, be very handy on ArbWiki as Wpuser:Sophie to provide all the background should this crop up again later (as I’m sure it will, either in the form of appeals or socks).” [emphasis mine]
Security concerns aside, the mailing list structure doesn’t seem to work. Even though list archives are kept, individual Arbitrators are relied on to forward old information.
“Do you have notes from your Feb 7 [CheckUser] of Guido that will help?”
“Does [anyone] have CU notes on Angela Kennedy or Destroying Angela they can forward to me?”
“Thank you for contacting us; the Committee is currently discussing your offer. Developing consensus among 18 or so people via mailing list isn’t terribly efficient, so we appreciate your patience.”
The leaks
A couple of users on Wikipedia Review, a forum critical of Wikipedia, have been posting email threads, largely based on requests. Why care? Actions on Wikipedia can have serious real world consequences. One of the emails details someone with a Wikipedia article being asked in a job interview about something untrue posted about him on Wikipedia. Another email talks about the power Wikipedia has over other search results, “if you were a sugar producer, how much would having [[Aspartame controversy]] be the first Google result for “artificial sweetener” be worth?” If you’ve ever used Wikipedia, as a reader or editor, what happens behind the scenes is relevant.
Note: some of the quoted emails are very old and I may be wrong in the conclusions I’ve drawn from them. Thanks to users at Wikipedia Review who did a great job pulling the interesting bits out of the emails in the forum threads.
Jimmy Wales versus an admin
A Wikipedia administrator called a user a “little shit” and was blocked from editing by Jimmy Wales for 3 hours. It’s unclear what harm a 3 hour block prevents and probably causes more drama than it solves. Arbitrators on the list raised concerns about Jimmy blocking users because of the attention those users receive as a result.
In emails Jimmy says he’d prefer a private mediation instead of a public Arbitration case:
“Indeed, if we go to a[n Arbitration case], I am going to push for [the removal of your administrator status], because I think you’ve gotten off very lightly so far, and your conduct since the block is very far out of line from what our community standards for admins are.
Whereas if you enter mediation and work with me, I think you’ll end up looking quite good. I am not a man of pride – I am willing to look bad if that will help Wikipedia in some way. Just come and work with me and with someone we both trust, and let’s at least try.”
In an email to the Arbitration Committee on the 22nd July 2009 Jimmy states that he’s giving up the block tool:
“I am hereby permanently giving up the use of the ‘block’ tool. I will remain an administrator so that I can do some other admin things from time to time (most importantly, viewing deleting revisions), so there is no need to do anything technical. I just won’t block anyone ever again.”
However, his actions log shows he performed a block in May 2010.
Threats against arbitrators
Forum user SB_Johnny summarizes an email that was eventually redacted by the leaker:
“Just for the benefit of the curious, a quick synopsis is that some asshole threatened to do harm to the loved ones (including children) of one of the [arbitrators] if the [arbitrator] didn’t do what he wanted. The other [arbitrators] (appropriately and gracefully) gave their moral and [emotional] support to the victim. ‘Nuff said on that.
The only thing that’s really of interest if that there wasn’t much in the way of support from Jimbo or the WMF [Wikimedia Foundation] (at least not in the dox provided), but only interesting in the sense that it was a rather alarming example of the sorts of things WMF volunteers are exposed to, and the WMF’s apparent disinterest in their fates.”
Hiding behind clerks
“Just to note that an anonymous IP (Comcast, Seattle Washington) has now posted an email from Lar (who has been broadly supportive of the proposals, including those relating to Jayjg), which implies that Lar himself is known to canvass. I am inclined to ask a clerk to delete as it is personal communication, but I do not think any of the committee members should do so. Thoughts?” [emphasis mine]
Experienced users versus new users
“Again it would be good enough to be used to justify a sock accusation against a new user, but it would be a world of pain for Arbcom to use it against a functionary who has broad support within the community (e.g. the reasonable recent election given he withdrew, with a growing cloud bearing down on him) and has ties with WMF (I’m not sure of all the details of this).”
Threats and blackmail by an ex-Arbitrator
“On 24 February 2010, FT2 contacted the Arbitration Committee by email to request return of Checkuser permissions for the purpose of participating in a specific sockpuppetry investigation. At that time, an email written by FT2 came to the attention of the entire Arbitration Committee. The email was addressed to an abusive sockpuppeter who had been banned from English Wikipedia and some other WMF projects as a result of a cross-wiki investigation in which FT2 played a significant role. In the email, FT2 threatened to contact family members of the sockpuppeter directly, and laid out a series of conditions including those external to Wikipedia with the threat of contacting employers, government agencies, and others about the nature of the socking.
It was known at the time this email was disclosed to the Committee ”en banc” that the conditions outlined in FT2’s email had not been met, and there was concern that he might proceed with the actions he had threatened in the email. FT2 confirmed that the text of the email was correct and implied that the content had been vetted in advance by a WMF staff member and a WMF board member. Both denied having read the email at any point.”
Here are some parts from that email:
“My conditions to you are simple. I will state them once, below. Failure to take this seriously will lead to the events changing from your rules and WR’s rules, to my rules. Hide one thing now or later, lie or evade once, and the gloves come off. Believe me, you don’t want to test that . That’s the advantage of being a volunteer rather than an employee. My only formal obligation is my own conscience, and the law.
They made errors like confusing your wife and sister. They don’t know about your children, whose names you put in the public domain and used as covers (which would disgust most people including your family). They don’t recognize that the [redacted]’ [his wife’s employer] IP means [redacted]’s [his wife’s] employer is legitimately fair to be brought into the frame to ascertain just what it extended to.
The bad news is, you have a choice: complete abject confession online to your online games, or exposure in your /offline/ world – it goes “real world” as the only way to kill it. You don’t get to keep both. Choose which.
One minute after that, gloves come off all the way, without any further warning, starting with [redacted]’s [his wife’s] workplace for evidence, and the Department of Health, and probably unavoidably, ending with family or someone will inform the police. Do you actually love your family, or need them? Or are they toys too?Sacrifice your fictions, games and abuses for yourself and them. Put right the abuses you have done over the last 3 years and you may survive, or take complete responsibility for any unfortunate results of forcible removal. I don’t know [his wife], but she seems tough, and people don’t like being deceived. I don’t know what settlement you’d get, but I bet it won’t include the things in real life you care most about. Risk it if you like. Your call. And watch me not minding if it hurts you to put this all right.Yes doing this is going to hurt and humiliate you. I couldn’t care less. No, avoiding hurt is not an option in life. You’re about to feel every last person you abused over 3 years, right now. You like editing, you don’t mind others hurting when you edit, so we’re going to edit my way a bit, if you want me to believe in any way that the matter is closed. The lesson here is, a wrong isn’t closed or an abuser off the hook till it’s put right and they commit not to repeat.
Then when that’s done you can fuck off to number 74 to reminiscence with [redacted list of family names] and the family. Or did you think I might be guessing at knowing far more than you thought? You put all that information on the web.By Monday noon EDT (ie Sept 15, 5pm UK, 6pm UTC I think), if you haven’t complied with at least #1 and are visibly in progress on #2 and #3, or there’s one sock you haven’t named, or I ever see one abusive edit after that from you under any name or proxy, the gloves come off for good with no more warning. We can talk as much as you like before then, but when that’s over, we’re done talking and I move on without further discussion if I don’t see a disclosure that I feel is honest and complete.
Others have contacted [redacted] and your workplace — shit happens, too bad, you did expect that, right? As for me, I plan to inform the last major group of victims, your family, not out of malice, but because they are ultimately the only ones who can prevent future abuse here, and recidivism.
You yourself dragged your wife [redacted], her employer [redacted], and your son [redacted] into this by yourself; they are in some ways the biggest victims of all and deserve to no longer be lied to or left ignorant of being taken as victims, as your co-worker [redacted], the beautician [redacted], your boss [redacted], the boudoir’s owner [redacted] whose business you placed at risk, and the rest were.” [emphasis mine]
Kind of takes serious business to the extreme. An Arbitrator says that “half dozen people had been [carbon] copied, including foundation folks. I thought the email was violently objectionable, but no one else seemed to mind. Maybe I’m bonkers?” If this is true, people from the Wikimedia Foundation knew about the content of the message and did nothing.
“No matter what they have done on-wiki, they don’t deserve that. [It’s] still ‘just a website’”—Understatement of the year from an Arbitrator.
Jimmy Wales gets involved and appears to refer to blackmail as “humanitarian kindness”:
“> I don’t know whether FT2 did that due to a momentary slip-up,
> illusions of grandeur, or actual malice. I don’t care whether his
> motivations were good or bad. I simply cannot give my imprimatur on
> him doing any sort of investigation on our site.
Just to be sure I was 100% clear the other day (I’ve been offline for several days due to a computer crash and illness) – I agree with you completely on this.
There are situations in which it could very much be ok to warn a user that continued misbehavior onsite could lead to offsite consequences. My own view is that such warnings should come at the point in which it would already be perfectly ok for us to publish the facts, and should be done as a humanitarian kindness and especially in cases where we think it is likely to be effective.
But this was really not ok at all.” [emphasis mine]
FT2 is still an administrator and has access to the OTRS system. OTRS volunteers deal with emails to a handful of email addresses on behalf of Wikipedia and the Wikimedia Foundation. In his own words:
“OTRS gets numerous emails under real names, describing real issues, legal claims, harassment, threats, and other matters.”
Perhaps concerningly, FT2 appears to actually be working for the Wikimedia Foundation now (from his user page), for time comparison, the above discussion was happening around early 2010.:
“In mid 2010 I was asked to spend time contributing to various projects at the Foundation’s offices, and in 2011 I was invited onto the WMF Communications Committee.”
Predators on my wiki? It’s more likely than you think
Or maybe just trolls and people trying to cause a PR crisis. Here’s the email the Arbitration Committee was going to send to the person in question:
You were asked several times by several Wikipedians interested in your welfare to downplay references to your self-reported age and your reported personal history as a “child porn victim”. Instead, it seems that each time someone asked you to tone things down, you went out of your way to promote yourself as “a little kid”. Your edit notices emphasized that you were “a little kid”, you posted both your age (13) and your reported date of birth on your userpage, and you added an image of a girl even younger than you as “decoration”. This was very provocative, as was explained to you.
The modified screenshot from /b/, an adult-only 4chan forum, that you posted on Jimbo Wales’ talk page again gave the appearance that you wanted to draw the attention of the /b/ editors, known for their vandalism of Wikipedia and their personal attacks directed at our editors. As you frequent the various Wikipedia-related IRC channels, you are well aware of the type of behaviour one can expect from /b/ participants. Your continual demands that people speak to you as if to a young child, posting even on heavily trafficked pages that you were “only 13”, was almost calculated to draw attention to yourself as a very young editor; in particular, your question of a high profile Arbitration Committee candidate, and the request for arbitration that you posted, seemed designed to bring your youthfulness to the attention of an ever-increasing audience. The emphasis on your desire to be spoken to like a child is very unusual behaviour for a 13-year-old girl.
Apart from your behaviour on-wiki, there have been increasing concerns and reports about the stories you have been telling other editors about yourself: that you were kidnapped and forced to do “child porn”; that you are in a witness protection program; that your school burned down so that is why you edit sometimes from [redacted] College, where some of your classes have been moved. (The only school fire reported in the [redacted] area in the past year resulted in the school’s kitchen being out of service for a day.) You have made references to the [redacted].org website, which you say is your father’s website; it’s registered to. He is also the same person who runs the “Help bring Madeline home” pages and you yourself have told me about the HBMH youtube page, which also is run by the same person, and which you say you were involved with.
I note with interest that two of the videos on that site are about internet safety for young people. And yet you would have us believe that your father/parents are oblivious to the fact that you are online until the wee hours of the morning UK time on a regular basis, talking to adult males in private IRC chat rooms, and cruising the 4chan /b/ channel. The moderator of the Youtube page, Steve, says his two daughters were kidnapped for six years, and returned in 2008; I’ve not heard of you mentioning a sister, just a brother, and I also note that there is not a single online news source that corroborates such an unusual case. This combination of stories doesn’t add up very well at all.
User:Sophie, I do not know if you are a 13 year old girl behaving provocatively, or someone pretending to be a 13 year old girl. Either way, the manner in which you have been participating on Wikipedia, starting off with the promotion of the [redacted].org site and now acting as a young child, is not conducive to our primary objective, the development of an encyclopedia.
Additionally “she” offers to provide a photograph of her holding a white board with the date on it to confirm her identity as a 13-year-old, but that she’s “scared of sending it to someone iv not spoken before.”
3. Sophie has presented photo identification to TechEssentials which has turned out to be fraudulent (it’s a copyrighted picture)
<Dusti> 4. In the beginning stages of [redacted].org child pornography was placed on the site.
Just to throw some more weirdness in there.
“Shouldn’t we just be reporting whoever is going around imitating a 13-year-old?”
Yes, great idea!
“Though I’m also aware that there are only two of us in the UK, and I would be reluctant to actually report anything myself, though I think something should be reported.”
No? Oh okay.
But really, predators
A pedophilia advocate was unblocked by the Arbitration Committee with a ban on editing articles about certain topics.
“We tacitly endorsed the continued editing of Davidwr last year. He came to our awareness when he asked permission for topic socks, fearful that editing on local topics could out him. We denied this arrangement, so he continued under his previous deal. He was unblocked a couple of years ago when Fred and FloNight negotiated his return with an unspoken topic ban. Lately, we’re not allowing a topic ban solutions at all. Given the risk of grooming, I think this makes sense.
The only distinguishing feature of Davidwr is that his pedo advocacy was done on an edit-segregated account, and the Davidwr account was swept up by Checkuser. Therefore, there’s no apparent evidence of
advocacy, but does it make sense to rely on this odd fact?” [emphasis mine]
Jimmy Wales  doesn’t want to say that pedophiles aren’t allowed to edit Wikipedia:
doesn’t want to say that pedophiles aren’t allowed to edit Wikipedia:
“At the same time, I am not willing that we should have a witch hunt for pedophiles or anyone else. Nor that we state, categorically, “pedophiles are not allowed to edit wikipedia” — I see no benefit to such a public stance.”
The issues above could have been discussed openly, or dealt with swiftly by actual staff from the Wikimedia Foundation (or wouldn’t have been issues if the ArbCom didn’t exist). In one of the emails Jimmy Wales says:
“To speak of traditionally “law” here, ArbCom is a delegation of my personal powers within the community since day one. I am free to dismiss ArbCom at will.”
Perhaps that’s a good idea.
Image credits: Renato Targa, William Brawley and Cary Bass
 Points I found interesting:
Points I found interesting:
 Déjà vu
Déjà vu Stuff reports
Stuff reports Notices from rights owners are sent to alleged infringers through their internet protocol address provider (effectively their internet service provider), like Telecom, Orcon and Slingshot. The order of the three notices (hence the three strikes name) are a detection notice, warning notice and then an enforcement notice. What notice you’re on is specific to each rights owner, eg. if you’re on the second notice, a warning notice, with
Notices from rights owners are sent to alleged infringers through their internet protocol address provider (effectively their internet service provider), like Telecom, Orcon and Slingshot. The order of the three notices (hence the three strikes name) are a detection notice, warning notice and then an enforcement notice. What notice you’re on is specific to each rights owner, eg. if you’re on the second notice, a warning notice, with 

 doesn’t want to say that pedophiles aren’t allowed to edit Wikipedia:
doesn’t want to say that pedophiles aren’t allowed to edit Wikipedia:

 A group of researchers have published a very interesting paper:
A group of researchers have published a very interesting paper: 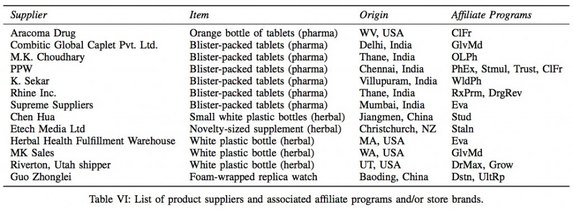
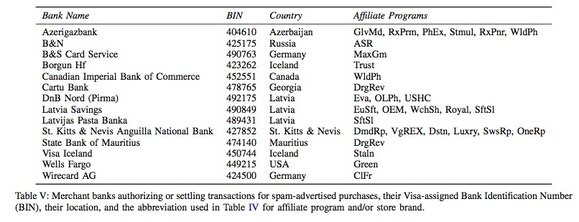 The researchers say that the banking/payment component of the spam value chain is the most critical. Payment infrastructure has “far fewer alternatives and far higher switching cost”.
The researchers say that the banking/payment component of the spam value chain is the most critical. Payment infrastructure has “far fewer alternatives and far higher switching cost”.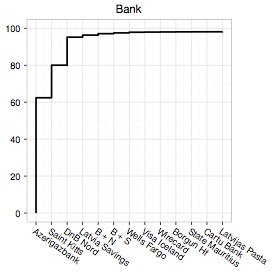
 HRC pressures King & Spalding to drop case defending the
HRC pressures King & Spalding to drop case defending the  Yesterday the
Yesterday the  (
(