Formspring recently reset lots of passwords after some were misplaced/stolen. Their email to users seems a little light on detail and doesn’t elaborate what the security reasons are, or even link to their own blog post about what happened. Sharing is caring, Formspring.
Category: Worldwide
Where Is The CCTV Footage From The Dotcom Mansion Raid?

Ars Technica sez:
“Since January, the Dotcom legal team has asked for the footage, but police refused, until finally the agency agreed that an IT expert for DotCom could come and collect a copy of the footage. When the IT expert arrived at the police station, he found the server completely disassembled, and authorities said they could not reassemble it or give him any footage. Now, no one outside the police agency is sure the footage still exists.”
Here’s what the Police said to me on 13 February:
“Police do not have any equipment which may hold this security footage. This equipment is held by the Official Assignee on behalf of the Crown, not Police.”
And here’s what the Insolvency & Trustee Service said on 17 February:
“The Official Assignee has no knowledge of any security camera footage.”
So what exactly does this footage show that the police and friends don’t want getting out?
Image credit: Charbel Akhras
I Know What You Downloaded Last Summer
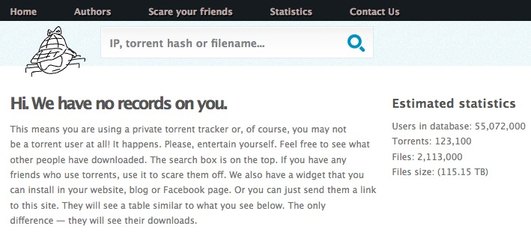
YouHaveDownloaded.com
An interesting site popped up near the end of last year called YouHaveDownloaded.com. You might not have visited it, or even heard of it, but if you’ve been using torrents, it might have heard of you.
The site is quite simple, it tracks torrents and the people (IP addresses) downloading them, much like copyright holders do (or hire companies to do for them). They claim to be tracking roughly 4%-6% of all torrent downloads and 20% of torrents from public trackers, like The Pirate Bay.
The difference to the copyright holders is that this site makes the information is collects public. You can see what it thinks the IP address you’re using has been used to torrent, or any other IP address you can think of. It might not be right, or it might be spot on.
This site just highlights what is going on all the time. Torrenting is a very public activity unless you’re making an effort to protect your privacy (like using a proxy or VPN from a reputable provider). Privacy is not the default on the interwebs.
IP addresses are more like PO Boxes than physical addresses — most people have dynamic IP addresses that regularly change, and add in the fact that some people have insecure Wi-Fi, the results on the site aren’t that accurate.
The site brings up an interesting statistic, especially if it’s true: “About 10% of all online shoppers, in the US, are torrent users as well.” In the future will advertisers link an IPs torrenting history to an advertising profile. Is this already happening?
The removal form
The site provides a form that supposedly enables people to request removal from the site. Don’t use it.
Previously it asked people to sign in using their Facebook accounts, and the CAPTCHA to get to the non-Facebook removal form didn’t work (ie. they wanted to link your data with a real name, cue warning bells). Now it seems like Facebook has revoked their access to use Facebook logins (they say Facebook logins are “Temporarily disabled due problems with Facebook”), so it brings up the removal form, which asks for a name and an email address.
I’m not saying this is what the people behind the site are doing, but this would be all the information they would need, in addition to the information they have on torrents associated with your IP address, to send an extortionate email your way. Or sell your data (probably not to copyright holders, because they hire people to do this for them already).
Here’s what their removal terms are (and yeah, the rest of the site is worded like this too):
“Removal Terms
The Details: By submitting a request to have your download activity removed from our database, you are acknowledging that the activity was, in fact, carried out by yourself. This means that you are only submitting a request to have the details of your own personal activity deleted. Any unrecognized activity, such as files you did not download or do not remember downloading, are not — I repeat, are not to be included in your removal request. Why is this imperative? Well, we actually don’t have to explain ourselves…sorry.The important part is that you understand these terms and conditions before hitting that beautiful button that will erase your criminal back ground, at least for now. Wait, you did remember to read these terms before making the decision to submit a removal request, right? Of course you did, everyone reads the fine print.
Other Important Things to Consider: We make no guarantees that your information will not appear on any other databases. We may have erased your bad behavior but, keep in mind that your data on this site is aggregated public domain. So, if by chance, another sadistic group of people decides to open a similar web site, we have no control over what they do with your information. Furthermore, if you continue to involve yourself in activity like this, your future download history will, without a doubt, appear in our database again and we may not be as nice about it next time.
If any part of these terms is still unclear, please visit your local elementary school and ask to repeat grades 3 through 5.”
Giving the people or company behind the site any more information about yourself is not a good idea, even if they claim that the site is a joke and you shouldn’t take it seriously.
And anyway, if your IP address is listed on the site, it must be because of the person that used it previously. Right?
The only redeeming feature of the site? You can look up the content companies that take people to court for illegal file sharing.
How To Counterfeit Money
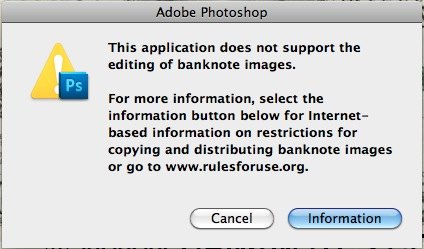
Not with Photoshop (and apparently Paint Shop Pro), or your printer, anyway.
The counterfeit deterrence system
If you try to open an image of specific currencies (and I assume at a specific resolution or higher) in Photoshop, you’ll receive the same error message as above. It’s interesting to note that New Zealand’s money isn’t blocked from being opened. Probably because we’re too busy trying to stop our passports from being counterfeited.
You can test it out using images from Banknotes.com. This one and this one throw up the error for me.
Here is Adobe’s information page on their ‘Counterfeit deterrence system’. What Photoshop is looking for is apparently a Digimarc digital watermark, different from the EURion constellation printers, or at least colour photocopiers look out for.
How to get around it
So what if your counterfeiting plans were going well so far, and now you’re at a standstill because of Adobe? You can use Gimp. It opens banknotes without trouble. So do old versions of Photoshop. And Microsoft Paint.
Why did Adobe think it was a good idea to add this? Counterfeiters will already know that they can use an older version of Photoshop, or use other software to get around this additional ‘feature’ and will be doing that.
All Adobe is doing is pissing off people who are trying to use Photoshop for a legitimate reason.
The Rules For Use website the dialog box directs users to even lists situations where you can reproduce banknotes legally (e.g. at a certain size), but Photoshop blocks opening banknotes full stop.
Why is it included?
Adobe will have had to spend time and money on including this system, with no returns in the form of additional sales. I assume they were pressured to include it, or even paid to include it by the Central Bank Counterfeit Deterrence Group.
Perhaps more concerning is that Adobe apparently has no idea what they have actually included in their software on behalf of the CBCDG:
“The inner workings of the counterfeit deterrence system are so secret that not even Adobe is privy to them. The Central Bank Counterfeit Deterrence Group provides the software as a black box without revealing its precise inner workings, Connor said.”
Secrecy
If you’ve bought Photoshop, were you aware of this system at the time of sale? You bought the software to open and edit images, but there are limitations you wouldn’t have been told about.
Here’s the two places where this system is talked about on Adobe’s website. A forum post and the information post linked to above.
Where’s the information page linked to from on Adobe’s website? My guess is not very many places, because they should have come up in the search too.
Printers are in on this too
I tried to print United States banknotes from Banknotes.com too. And the job failed. Here’s a New Zealand banknote that printed (and scanned) fine, with one of the United States notes below, which stopped printing halfway through.

Here’s the error message in the print dialog.
![]()
Error 9707 seems to be specific to the counterfeit deterrence system, but is only described as “reading pixels failed”.
So I guess every time I print something, either the printer or the driver is all: “IS THIS LOOK LIKE MONEY?! NOPE, SEEMS TO BE A GIRAFFE.”
What I wonder is what other, potentially less visible and transparent “features” are being included in systems because of pressure or money?
I don’t want manufacturers including these non-features in their products for me and I don’t want my technology making decisions for me.
Stop Sugercoating Bullying

The Children’s Healthcare of Atlanta has been running their Strong4Life campaign since May 2011.
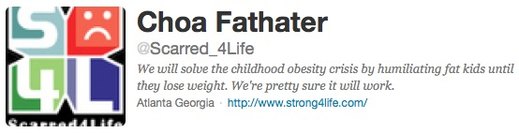
This is a parody Twitter account, but the bio is spot on. Here’s a selection of advertisements they have been running:


You can watch similar TV spots they have run on their YouTube channel.
Rather than focusing on encouraging healthy behaviors, the ads shame and stigmatize overweight kids.
“What psychologist would think shame and bully ads would be effective?”
None were consulted in the ad campaign creation process:
@5minutesformom No – child psychologists were not part of the creation of the ad campaign. Focus groups with parents were.
— Strong4Life (@strong_4_life) January 28, 2012
So why did they think these ads were a good idea?
“The hard-hitting tone of Children’s Healthcare’s ads were inspired by Georgia METH Project’s ‘Not Even Once’ campaign.”
Because anti-meth ads using the same techniques worked.
Because meth users and kids who are overweight (wait, the ads are targeted at the parents, not the kids!) have so much in common. WHY WOULDN’T IT WORK??
Strong4Life thinks that the ads are okay, because only parents will see them. Not children.
@calledoutrev The ad campaign is targeted toward parents and caretakers- not the children.
— Strong4Life (@strong_4_life) January 6, 2012
Not sure how they come to this conclusion.
From an actual psychologist, Dr Rebecca Puhl, director of research and weight stigma initiatives at the Rudd Center for Food Policy & Obesity at Yale University:
“There seems to be this perception that it’s OK to shame children and families struggling with obesity because that will provide an incentive to lose weight. However, research in weight bias shows that when individuals feel shamed or stigmatized because of weight they’re actually more likely to engage in behaviors that reinforce obesity: unhealthy eating, avoidance of physical activity, increased caloric intake.”
“Alan Guttmacher, director of the Institute of Child Health and Human Development, agreed that the Strong4Life campaign ‘carries a great risk of increasing stigma’ for overweight and obese children.”
The original TV ads stopped airing, but there’s a new one out as of a couple of weeks ago. Most of the billboards have come done, and apparently the rest will come down in March.
“The stigma itself needs to be addressed itself because until we do that, why would a fat child want to go out on the playground and be teased? We want to create an environment where people are not treated so poorly because of their bodies that they’ll want go out and enjoy physical movement.” – Amy Farrell, author of “Fat Shame: Stigma and the Fat Body in American Culture” and a professor of American studies and Women’s & Gender Studies at Dickinson College.
The National Eating Disorders Association called for Children’s Healthcare of Atlanta to “dimantle [the] alarming, anti-obesity ad campaign that targets and shames children.”
“The ad campaign is most successful at shaming youth who are overweight and reinforcing societal prejudice against children who do not have an ‘ideal’ body type.” “Every day we hear about the terrible rise in bullying within our schools, yet this ad campaign could actually promote and give permission to such behaviors among kids. Sadly, these ads will be successful in shaming children with weight problems and their parents, but will do nothing to promote and educate about wellness and emotional well-being.” “As many as 65% of people with eating disorders say bullying contributed to their condition.”
“Shame on Children’s Healthcare of Atlanta … not shame on the local kids.”
And also, what were the parents of the children in these ads thinking?
“Where would your government be without child porn?”
“If it didn’t exist, the government would surely invent it.”
Because it’s a great excuse for an internet censorship machine.
This isn’t a debate about whether child sex abuse is right or wrong. You know it’s wrong, I know it’s wrong, we all know it’s wrong. This is a debate about censorship.

New Zealand has an internet blacklist. A list of content that, if your internet service provider has decided to be part of the filtering project, you can’t access. Images of child sexual abuse are meant to be the only stuff blocked, but the list is secret, censorship decisions happen in private and if international experience is anything to go by, other content has a habit of turning up blacklisted.
What the filter is
Its full name is the Digital Child Exploitation Filtering System. It’s run by the Department of Internal Affairs. It’s powered by NetClean’s WhiteBox, which was supplied by Watchdog International “which provides filtered Internet access for families, schools and businesses”.
The DIA say that they’re contractually constrained to only use the filter to block child sexual abuse material.
“The filtering system is also a tool to raise the public’s awareness of this type of offending and the harm caused to victims. The Group agreed that this particular aspect of the filter needs to be more clearly conveyed to the public.”
So basically, it’s to make it seem like they’re doing something, because it doesn’t actually prevent people from accessing child sex abuse images.
The list is maintained by three people (pdf) (mirror), and sometimes there is a backlog of sites to investigate: “The Group was advised that the filter list comprises approximately 500 websites, with several thousand more yet to be examined.”
How it works
A list of objectionable sites is maintained by the Department. If someone using an ISP that’s participating in the filter tries to access an IP address on the filter list, they’ll be directed to the Department’s system. The full URL will then be checked against the filtering list. If the URL has been filtered, users end up at this page. The user can appeal for the site to be unfiltered, but no appeals have been successful yet (and some of the things people have typed into the appeal form are actually quite disturbing).
Is my internet being filtered?
The internet of 2.2 million ISP clients is being filtered.
It’s voluntary for ISPs to participate in because it wasn’t introduced through legislation, however big ISPs are participating:
- Telecom
- TelstraClear
- Vodafone
- 2degrees
Others are:
- Airnet
- Maxnet
- Watchdog
- Xtreme Networks
I assume, for the ISPs providing a mobile data service, the filter is being applied there too.
Why the filter is stupid
Child pornography is not something someone stumbles upon on the internet. Ask anyone who has used the internet whether they have innocently stumbled upon it. They won’t have.
It’s easy to get around. The filter doesn’t target protocols other than HTTP. Email, P2P, newsgroups, FTP, IRC, instant messaging and basic HTTPS encryption all go straight past the filter, regardless of content. Here’s NetClean’s brochure on WhiteBox (pdf), and another (pdf). Slightly more technical, but still basic tools like TOR also punch holes in the filter. The filter is not stopping anyone who actually wants to view this kind of material.
A much more effective use of time and money is to try to get the sites removed from the internet, or you know, track down the people sharing the material. Attempts to remove child sex abuse material from web hosts will be supported by a large majority of hosts and overseas law enforcement offices.
It is clear that the DIA don’t do this regularly. They’re more concerned with creating a list of URLs.
From the Independent Reference Group’s December 2011 report:
“Additionally 18% of the users originated from search engines such as google images.”
Google would take down child sex abuse images from search results extremely fast if they were made aware of them. And it is actually extremely irresponsible for the DIA not to report those images to Google.
Update: The DIA say they used Google Images as an example, and that they do let Google know about content they are linking to.
“The CleanFeed [the DIA uses NetClean, not Cleanfeed] design is intended to be extremely precise in what it blocks, but to keep costs under control this has been achieved by treating some traffic specially. This special treatment can be detected by end users and this means that the system can be used as an oracle to efficiently locate illegal websites. This runs counter to its high level policy objectives.” Richard Clayton, Failures in a Hybrid Content Blocking System (pdf).
It might be possible to use the filter to determine a list of blocked sites, thus making the filter a directory or oracle for child sex content (however, it’s unlikely people interested in this sort of content actually need a list). Theoretically one could scan IP addresses of a web hosting service with a reputation for hosting illegal material (the IWF have said that 25% of all websites on their list are located in Russia, so a Russian web host could be a good try). Responses from that scan could give up IP addresses being intercepted by the filter. Using a reverse lookup directory, domain names could be discovered that are being directed through the filter. However, a domain doesn’t have to contain only offending content to be sent through the DIA’s system. Work may be needed to drill down to the actual offending content on the site. But this would substantially reduce the effort of locating offending content.
Child sex abuse sites could identify DIA access to sites and provide innocuous images to the DIA and child sex abuse images to everyone else. It is possible that this approach is already happening overseas. The Internet Watch Foundation who run the UK’s list say in their 2010 annual report that “88.7% of all reports allegedly concerned child sexual abuse content and 34.4% were confirmed as such by our analysts”.
Someone could just use an ISP not participating in the filter. However people searching for this content likely know they can be traced and will likely be using proxies etc. anyway. Using proxies means they could access filtered sites through an ISP participating in the filter as well.
It is hard (practically, and mentally) for three people to keep on top of child sex abuse sites that, one would assume, change locations at a frequent pace, while, apparently, reviewing every site on the list monthly.
The filter system becomes a single point of attack for people with bad intentions.
The DIA, in their January 2010 Code of Practice (pdf) even admit that:
- “The system also will not remove illegal content from its location on the Internet, nor prosecute the creators or intentional consumers of this material.” and that
- “The risk of inadvertent exposure to child sexual abuse images is low.”
Anonymity
The Code of Practice says:
“6.1 During the course of the filtering process the filtering system will log data related to the website requested, the identity of the ISP that the request was directed from, and the requester’s IP address.
6.2 The system will anonymise the IP address of each person requesting a website on the filtering list and no information enabling the identification of an individual will be stored.”“6.5 Data shall not be used in support of any investigation or enforcement activity undertaken by the Department.” and that
“5.4 The process for the submission of an appeal shall:
• be expressed and presented in clear and conspicuous manner;
• ensure the privacy of the requester is maintained by allowing an appeal to be lodged anonymously.”
Anonymity seems to be a pretty key message throughout the Code of Practice.
However…
In response to an Official Information Act request, the DIA said:
“When a request to access a website on the filtering list is blocked the system retains the IP address of the computer from which the request originated. This information is retained for up to 30 days for system maintenance releases and then deleted.” [emphasis mine]
Update: The DIA says that the IP address is changed to 0.0.0.0 by the system.
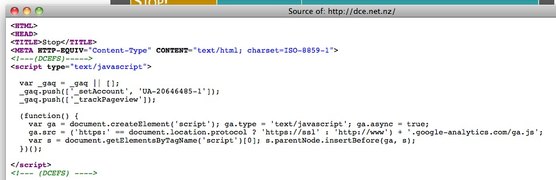
The site that people are directed to when they try to access a URL on the blacklist (http://dce.net.nz) is using Google Analytics. The DIA talk the talk about the privacy and anonymity around the filter, but they don’t walk the walk by sending information about New Zealand internet users to Google in the United States. It’s possible this is how the DIA gets the data on device type etc. that they use in their reports. Because anyone can simply visit the site (like me, just now) those statistics wouldn’t be accurate.
From the Independent Reference Group’s August 2011 (pdf) minutes:
“Andrew Bowater asked whether the Censorship Compliance Unit can identify whether a person who is being prosecuted has been blocked by the filtering system. Using the hash value of the filtering system’s blocking page, Inspectors of Publications now check seized computers to see if it has been blocked by the filtering system. The Department has yet to come across an offender that has been blocked by the filter.”
I’m not exactly sure what they mean by hash value, but this would seem to violate the “no information enabling the identification of an individual will be stored” principle.
Update: They are searching for the fingerprint of content displayed by the blocking page. It doesn’t seem like they could match up specific URL requests, just that the computer had visited the blocking page.
And, from the Independent Reference Group’s April 2011 (pdf) minutes:
“For all 4 of the appeals the complainant did not record the URL. This required a search of the logs be carried out to ensure that the site was correctly being blocked.”
Appeals are clearly not anonymous if they can be matched up with sites appellants have attempted to access.
Update: The reviewers look at the URLs blocked shortly before and after the appeal request to work out the URL if it isn’t provided.
9000 URLs!
The DIA earlier reported that there were 7000+ URLs on their blacklist. This dropped to 507 in April 2011, 682 in August 2011, and 415 in December 2011. Those numbers are much closer to the 500 or so URLs on IWF’s blacklist.
Where did these 6500 URLs disappear to (or more accurately, why did they disappear?). What was being erroneously blocked during the trial period, or was 7000 just a nice number to throw around to exaggerate the likelihood of coming across child sex abuse images (though, even with 7k sites, the likelihood still would have been tiny)?
Scope creep
Firstly, we weren’t going to have a filter at all:
‘“We have been following the internet filtering debate in Australia but have no plans to introduce something similar here,” says Communications and IT minister Steven Joyce.
“The technology for internet filtering causes delays for all internet users. And unfortunately those who are determined to get around any filter will find a way to do so. Our view is that educating kids and parents about being safe on the internet is the best way of tackling the problem.”’
Then it was said that:
“The filter will focus solely on websites offering clearly illegal, objectionable images of child sexual abuse.”
and
“Keith Manch said the filtering list will not cover e-mail, file sharing or borderline material.” [emphasis mine]
One would assume from “images of child sexual abuse” that they would be, you know, images of children being sexually abused. However, it seems that CGI and drawings (Hentai) have made the list.
From the minutes of the Independent Reference Group’s October 2010 meeting:
“Aware that the inclusion of drawings or computer generated images of child sexual abuse may be considered controversial, officials advised that there are 30 such websites on the filtering list [that number is now higher, 82 as of December 2011]. Nic McCully advised that officials had submitted computer generated images for classification and she considered that only objectionable images were being filtered.”
The arguments around re-victimization kind of fall apart when you’re talking about a drawing.
And from the borderline material file:
“The Group was asked to look at a child model website in Russia. The young girl featured on the site appears in a series of 43 photo galleries that can be viewed for free. Apparently the series started when the girl was approximately 9 years old, with the latest photographs showing her at about 12 years old. The members’ part of the site contains more explicit photos and the ability to make specific requests. While the front page of the website is not objectionable, the Group agreed that the whole purpose of the site is to exploit a child and the site can be added to the filter list.”
Clearly illegal, objectionable images of child sexual abuse? No, but we think it should be filtered so we went and did that.
Dodgy DIA
The DIA was secretive about the filter being introduced in the first place. Their first press release about it was two years after a trial of the system started. I wonder how many of those customers using an ISP participating in the trial knew their internet was being filtered during that time?
The Independent Reference Group is more interesting than independent. Steve O’Brien is a member of the group. He’s the manager of the Censorship Compliance Unit. To illustrate this huge conflict of interest, he is the one who replies to Official Information Act requests about the filter. Because the Censorship Compliance Unit operate it.
“The Group was advised that the issue of Steve O’Brien’s membership had been raised in correspondence with the Minister and the Department. Steve O’Brien offered to step down if that was the wish of the Group and offered to leave the room to allow a discussion of the matter. The Group agreed that Steve O’Brien’s continued membership makes sense.” [emphasis mine]
That was the only explanation given. That it makes sense that he is a member. Of the group that is meant to be independent.
Additionally, the DIA seems to have accidentally deleted some reports that they should have been keeping.
“Last year we used the Official Information Act to ask for copies of the reports that the inspectors [have] used to justify banning the websites on the list. The DIA refused. After we appealed this refusal to the Ombudsman, the DIA then said that those records had been deleted and therefore it was impossible for them to give them to us anyway. The Department has an obligation under the Public Records Act to keep such information.
We complained to the Chief Archivist, who investigated and confirmed that the DIA had deleted public records without permission. He told us that the DIA has promised to do better in the future, but naturally this didn’t help us access the missing records.”
List review
The Code of Practice says:
“4.3 The list will be reviewed monthly, to ensure that it is up to date and that the possibility of false positives is removed. Inspectors of Publications will examine each site to ensure that it continues to meet the criteria for inclusion on the filtering list.”
It’s unlikely this actually happens.
Here’s some statistics of how many URLs have been removed.
December 2011
267 removedAugust 2011
0 removedApril 2011
108 removed
It’s impossible that between April and August there were no URLs to remove.
In the Independent Reference Group’s December 2011 report it seemed like the following was included because it happens so rarely:
“The list has been completely reviewed and sites that are no longer accessible or applicable (due to the removal of Child Exploitation Material) have been removed.”
The Independent Reference Group has the power to review sites themselves. But in at least one case, they chose not to:
“Members of the Group were invited to identify any website that they wish to review. They declined to do so at this stage.”
The filter isn’t covered by existing law and didn’t pass through Parliament. Appropriate checks and balances have not taken place. The DIA did this on their own.
By law, the Classification Office has to publish its decisions, which they do. The DIA’s filter isn’t covered under any law, and they refuse to release their list. The DIA say that people could use the list to commit crimes, but the people looking for this material will have already found it.
What if the purpose of the filter changes? The DIA introduced it without a law change, the DIA can change it without a law change. What if they say “if ISPs don’t like it, they can opt out of the filter”? How many ISPs will quit?
The only positive is that the filter is opt in for ISPs. Please support the ISPs that aren’t using the filter. Support them when they’re accused of condoning child pornography, and support them when someone in government decides that the filter should be compulsory for all ISPs.
Side note: why does all of the software on the DIA’s family protection list, bar one, cost money? There is some excellent, or arguably better, free software available. There’s even a free version of SiteAdvisor, but the DIA link to the paid one. Keep in mind that spying on your kids is creepy. Talk to them, don’t spy. The video for Norton Online Family hilariously and ironically goes from saying “This collaborative approach makes more sense than simply spying on your child’s internet habits [sitting down and talking — which is absolutely correct]” to talking about tracking web sites visited, search history, social networking profiles, chat conversations and then how they can email you all about them. Seriously. Stay away.
Image credit: Andréia Bohner
Congratulations Internets
But your work is not over.
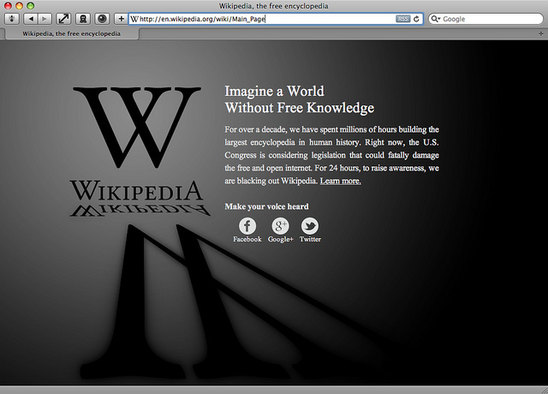
On January 18 the users and companies of the internet rallied together to protest against SOPA and PIPA, bills that would censor the internet. Check out the numbers. It worked. Here‘s part of a huge list, with even bigger names on it of the sites that participated in the blackout. Google, Wikipedia, Reddit, BoingBoing and Wired are among them. Here’s the page Wikipedia displayed. The Wikipedia page about SOPA and PIPA was accessed more than 162 million times during the 24 hours the site was blacked out. More than eight million people looked up their elected representatives’ contact information via Wikipedia’s tool, crashing the Senate’s website. At one point, 1% of all tweets on Twitter included the #wikipediablackout hashtag.
SOPA? PIPA?
- Wikipedia explains, and has some links here.
- One page PDF guide to the bills from EFF
Is it over?
It is likely the bills will be back in one form or another:
What’s the best way for me to help? (for U.S. citizens)
The most effective action you can take is to call your representatives [phone calls have the most impact] in both houses of Congress, and tell them you oppose SOPA, PIPA, and the thinking behind them.[9]
What’s the best way for me to help? (for non-U.S. citizens)
Contact your country’s Ministry of Foreign Affairs or similar government agency. Tell them you oppose SOPA and PIPA, and any similar legislation. SOPA and PIPA will affect websites outside of the United States, and even sites inside the United States (like Wikipedia) that also affect non-American readers — like you. Calling your own government will also let them know you don’t want them to create their own bad anti-Internet legislation.
For New Zealanders, that’s the Ministry of Foreign Affairs and Trade. Their contact details are here.
Megaupload
Megaupload’s website was taken down a day after the protest (without trial), with related people being arrested in New Zealand, and property confiscated. Are we okay with helping enforce US copyright law which, as SOPA and PIPA shows is heavily influenced by the entertainment industry? Is this what extradition should be used for?
It appears, at first glance, that Megaupload was removing infringing material on request. Although it seems their take down procedure was molded around the way they store files–only storing one copy of it if it is uploaded more than once, but giving out a unique URL for the file.
Megaupload has many similarities to other websites, which makes this concerning. It was definitely used for legitimate and legal purposes by legitimate users.
Tech Liberty asks do we need to obey laws from other countries while on the internet, if so, what countries?
Even if I have a web host in one country, what if they provide services via another country? The internet is so connected, how do we know whose laws apply?
Image credit: LoveNMoreLove/Wikipedia

Internet Censorship Is Harmful
I’m on holiday and posting this from my phone. Let’s all pretend this site is blacked out.
Image credit: Jed Hastwell
PayPal Policy Update Strangeness
PayPal send out emails about policy updates. Here is one of them:
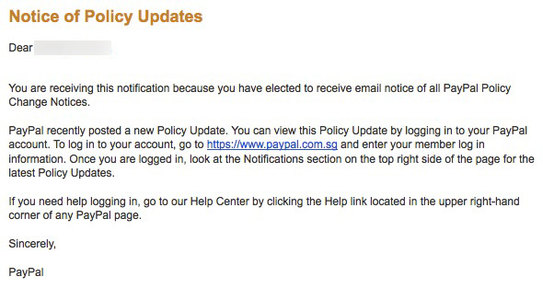
There’s a few strange things going on.
1) I’m not in Singapore but get sent their Singapore address.
2) They link to their site when they could have just said “go to PayPal’s website”. Getting people into the habit of clicking on links asking them to log in, especially ones with weird extensions doesn’t seem good.
3) If you’re going to include a link, at least link to the changes. Why do I have to log in and go to notifications to see them?
4) On the same note, why aren’t the changes just included in the email to begin with?
Here’s one of the changes listed in notifications:
It is the whole PayPal User Agreement. What has changed? Who knows.
To their credit, a more recent January change just has the part of the policy that has changed.
Maybe they’re learning.
Financial Advice

Here is a New Zealand Herald article that contains some shitty and some good advice about money.
Thumbs down
Buying over renting
Buy property young, preferably in your 20s. Move heaven and earth to get the deposit. Rent is wasted money.
Buying a house is not for everyone. Sometimes it doesn’t make financial sense for a particular person. Insurance, rates, money spent on repairs (~$5k~ a year) etc. sometimes make renting a better choice. Run the numbers.
Avoid fines
It’s moronic to incur fines. Like the maniac driver in a big red American-style pickup truck who overtook me on State Highway 2 on December 17, just to be pulled over and fined.
Yes, you shouldn’t speed etc. etc., but this doesn’t contain any useful advice if you do get a fine. Actual advice would be to set up an automatic payment account to a ‘Stupid mistakes’ savings account so you have money to pay inevitable fines.
NEVER SPEND MONEY EVAAAA
Every dollar is precious. Think before you spend it.
I regret frittering money on coffees and unnecessary eating out. It would be better to direct that money towards savings.
Needs and wants are often confused. This is perhaps the biggest financial mistake that people make.
If you enjoy a coffee a day, buy a coffee a day. If you enjoy eating out, eat out. There’s no point earning money if you don’t spend it on stuff you love. Cut back on the stuff you don’t care about, optimize existing spending (subscriptions and phone/internet/TV/power etc. plans) and/or earn more money.
Have a budget!!@@111
Track your spending. You can’t budget if you don’t know what you’re spending.
Perhaps the most popular piece of financial advice ever given out. How many people who write this actually do in it in practice, I’m not sure. Tracking your spending by typing into a spreadsheet or basically anything with mainly manual entry is doomed to fail. Xero with BNZ and ASB by itself both offer spending tracking services within online banking. Or, Xero allows the import of other bank’s transactions. Do mainly electronic transactions (because they can automatically coded into categories) and use these.
Credit cards
Credit cards make you look rich. Anyone can live well for a few years, but the debt catches up.
Credit cards with benefits that are automatically paid off each month are excellent.
Thumbs up
Judging people
People are too quick to judge others’ financial decisions, me included.
1) No one wants unsolicited advice. 2) You have your own problems to worry about.
Pay bills
Pay your taxes on time. The IRD has a big stick.
Pay all bills on time. Automate them. The IRD and other companies are always up for negotiation around deadlines.
Experiences
Spending money on experiences is good spending. I am eternally grateful that I sold all but one of my shares at age 22 (by coincidence in August 1987) and went backpacking through Latin America. It’s good spending if the experience enriches life.
Yes. Also, give experiences as presents instead of physical things.
Save for things. Automatically.
Save before you buy. A bit of a radical concept in 2011, but it can change people’s financial future.
Enter into interest-free deals cautiously
Interest-free hire purchase deals are for suckers. You still pay ad establishment fee and the majority of people fail to clear the debt on time and pay interest anyway.
These places invariably have great clauses such as charging you if you pay anything over the set monthly amount. Once you’ve finished paying the item off you get mailed offers from the company for ever and ever.
Avoid interest
Interest payments on personal loans, credit cards and HP are “idiot tax”. Why throw money away unnecessarily?
Work out how much something will really cost when interest is added before jumping into these. There’s calculators online that will help.
KiwiSaver
KiwiSaver is good.
Get in it.
Advice
Take your advice from people who have been through several cycles. Johnny-come-latelies going through their first financial cycle underestimate the risks.
Ask older people what they would have liked to have known at your age. What would they save for if they could turn back the clock?
Read a book
You can learn more about money. The easiest and cheapest way to improve your knowledge is to get a book out of the library.
Image credit: 401k/401kcalculator.org